Configure Enterprise State Roaming in Azure AD
Windows 10 users who use a Microsoft account can sync their user settings, Microsoft Edge browser passwords, and application settings between devices that use the same Microsoft account.
For enterprise users, Azure Active Directory provides the roaming functionality. Administrators can enable an enterprise feature called Enterprise State Roaming to allow Azure AD to securely synchronize users’ Windows settings, passwords, and Universal Windows Platform (UWP) app settings and data across their Windows devices. With their profile settings stored in the cloud, the settings can be automatically applied to a new device following sign-in.
In addition to the settings that are included in the consumer-facing Sync settings, Enterprise State Roaming offers the following additional functionality:
- Separation of corporate and consumer data There is no mixing of corporate data and consumer data. Each cloud account holds data separately.
- Enhanced security Using Azure Rights Management protection, data is always encrypted, both in transit and while at rest.
- Better management and monitoring The Azure AD portal provides control and visibility over which users and devices have their settings synced.
- Data retention Enterprise State Roaming data that has been synced to Azure is retained for between 90 and 180 days after it was last accessed.
For an organization to use Enterprise State Roaming, it must meet the following requirements:
- Windows 10 Version 1511 (OS Build 10586 or later), with the latest updates installed on the device.
- Devices must be Azure AD–joined or hybrid Azure AD–joined.
- Enterprise State Roaming must be enabled for the tenant in Azure AD.
- Users must already be assigned an Azure AD Premium or Enterprise Mobility + Security (EMS) license.
- Devices must be restarted following the enabling of Enterprise State Roaming.
- Users must sign in using an Azure AD identity.
Once the Enterprise State Roaming feature is enabled, the organization is granted a free, limited-use license to use Azure Rights Management protection in Azure Information Protection. This license is limited to encrypting and decrypting enterprise settings and application data synced by Enterprise State Roaming.
To enable Enterprise State Roaming within Azure, follow these steps:
- Sign into the Azure Active Directory admin center at https://aad.portal.azure.com/ using a global administrator account.
- Select Azure Active Directory, and then under Manage, click Devices.
- On the Devices–All Devices blade, click Enterprise State Roaming.
- On the Devices–Enterprise State Roaming page, configure the Users may sync settings and app data across devices option to suit your organizational needs. You can enable roaming for all users or for only a selected group of users, as shown in Figure 2-15.
- Click Save.
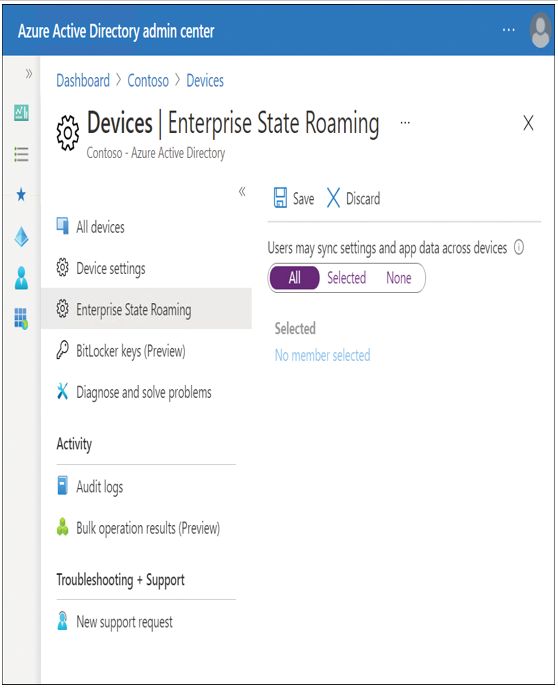
Figure 2-15 Configure Enterprise State Roaming
Exam Tip
You should ensure that you fully understand how to modernize user profile management. Solutions such as OneDrive for Business, deploying Known Folder Move, and enabling Enterprise State Roaming are likely to be featured on the exam. By forcing user profiles and data to be moved to the cloud, the data is then stored securely and managed by using MDM.
Once the Azure AD settings have been configured, your Windows 10 devices need to be restarted, and the user needs to authenticate using the user’s primary sign-in identity.
Need More Review? Enterprise State Roaming in Azure Active Directory
If you want to know how to configure and troubleshoot Enterprise State Roaming in Azure Active Directory, use this Microsoft website: https://docs.microsoft.com/en-us/azure/active-directory/devices/enterprise-state-roaming-enable.
All user settings and application settings data synced to the Microsoft cloud using Enterprise State Roaming are retained for a period based on the rules shown in Table 2-13.
TABLE 2-13 Enterprise State Roaming data retention
| GPO setting | Description |
| Explicit deletion | User Deletion When an Azure AD user account is deleted, the user account roaming data is deleted after 90 to 180 days. Directory Deletion After deletion of an entire directory in Azure AD, all the settings data associated with that directory is deleted after 90 to 180 days. On Request Deletion An Azure AD admin can file a ticket with Azure support to manually delete a specific user’s data or settings data. |
| Stale data deletion | User account roaming data that has not been accessed for one year will be treated as stale and may be deleted from the Microsoft cloud. The retention period is subject to change but will not be less than 90 days. The stale data is based on the following criteria: If no devices access a settings collection, such as a specific app setting or Windows 10 Theme, then that collection becomes stale after the retention period and may be deleted. If a user disables settings sync on his or her device, then all the settings data for that user will become stale and may be deleted after the retention period. If Enterprise State Roaming is disabled for the entire directory, then settings syncing will stop. All settings data for all users will become stale and may be deleted after the retention period. |
| Deleted data recovery | The Enterprise State Roaming data retention policy is not configurable. Once the sync data is deleted, it is not recoverable. The data deletion only applies to the Microsoft cloud and not from the user device. If a device later reconnects to the Enterprise State Roaming service, the device-based settings will be synced and stored in the Microsoft cloud. |