Implement Network Protection
Network Protection helps you to prevent your users from using apps to access internet-based domains that might present a risk of malware, scams, or other malicious content. You can use GPOs, mobile device management (MDM) policies, or Windows PowerShell to enable Network Protection. To use GPOs, use the following procedure:
- On a domain controller, open the appropriate GPO for editing.
- In the Group Policy Management Editor, navigate to Computer Configuration > Policies > Administrative Templates > Windows Components > Microsoft Defender Antivirus > Microsoft Defender Exploit Guard > Network Protection.
- Select Prevent users and apps from accessing dangerous websites.
- Select Enabled, and then select one of the following:
- Block Users cannot access malicious sites.
- Disable Network Protection is not functional.
- Audit Mode Tracks activity but does not block access to malicious sites.
- Select OK, and then close the Group Policy Editor.
To use Windows PowerShell (Administrator), use the Set-MpPreference cmdlet. For example, to enable Network Protection in Audit Mode, use the following command:
Click here to view code image
Set-MpPreference -EnableNetworkProtection AuditMode
Available options are Disabled, AuditMode, and Enabled.
Need More Review? Enable Network Protection
To review further details about enabling and configuring Network Protection, refer to the Microsoft website at https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/network-protection.
Implement Controlled Folder Access
You can use Controlled Folder Access to help prevent the spread of malicious software. Specifically, Controlled Folder Access helps protect valuable data stored in specific folders. You can use Windows PowerShell, GPOs, or MDM to configure Controlled Folder Access.
To use GPOs to manage Controlled Folder Access, use the following procedure:
- On a domain controller, open the appropriate GPO for editing.
- In the Group Policy Management Editor, navigate to Computer Configuration > Policies > Administrative Templates > Windows Components > Microsoft Defender Antivirus > Microsoft Defender Exploit Guard > Controlled Folder Access.
- Double-click the Configure Controlled folder access setting, as displayed in Figure 3-7, and select Enabled.
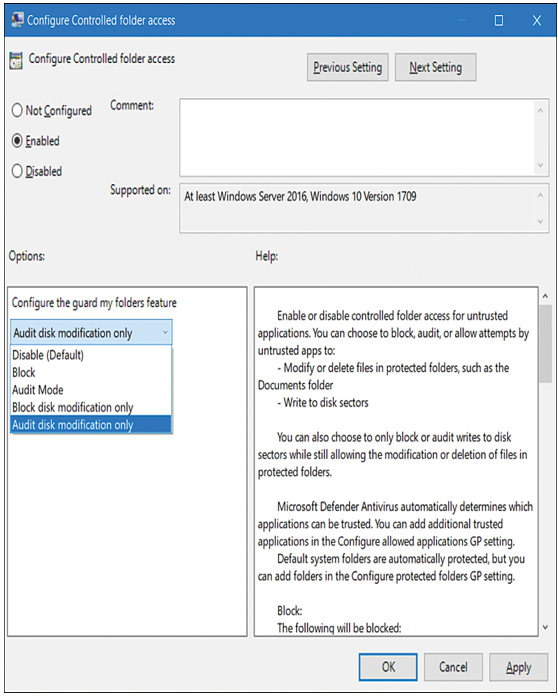
Figure 3-7 Enabling Controlled Folder Access
4. In the Configure the guard my folders feature list, select one of the following:
- Disable This stops the Controlled Folder Access feature.
- Block Suspicious or malicious software cannot make changes to protected folders.
- Audit Mode Tracks rather than prevents changes to protected folders.
- Block disk modification only Prevents untrusted apps from writing to disk sectors.
- Audit disk modification only Audits untrusted apps that write to disk sectors.
5. Select OK and then close the Group Policy Management Editor.
To use Windows PowerShell (Administrator) to configure Controlled Folder Access, use the Set-MpPreference cmdlet. For example, to enable Controlled Folder Access, enter the following PowerShell command:
Click here to view code image
Set-MpPreference -EnableControlledFolderAccess Enabled
Available options are Disabled, AuditMode, and Enabled.
After you have enabled Controlled Folder Access, you must also specify the Trusted Apps and Protected Folders settings as well. By default, Windows protects a number of folders, including system folders and default locations, such as Documents, Pictures, Movies, and Desktop.
You can configure additional folders using the Windows Security app, GPOs, Windows PowerShell, and MDM. To use the Windows Security app, use the following procedure:
- Open the Windows Security app and select the Virus & Threat Protection tab.
- Select the Manage Ransomware Protection link.
- If Controlled Folder Access is not already enabled, select On.
- Select the Protected folders link shown in Figure 3-8.
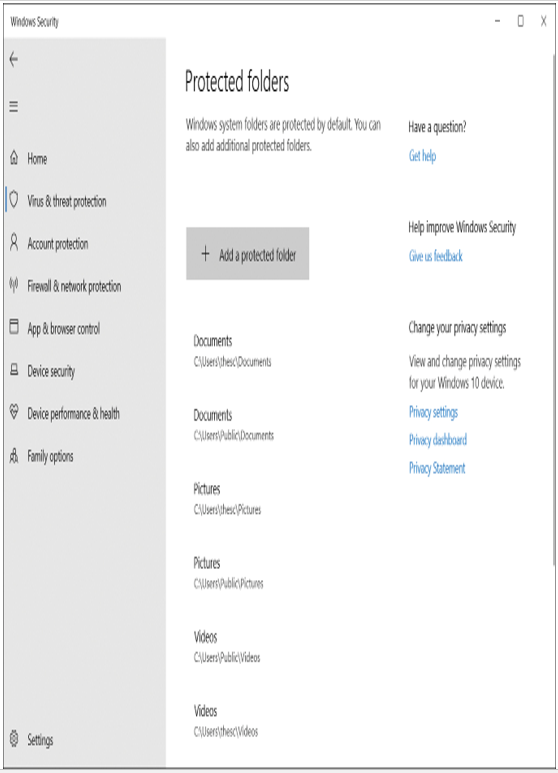
Figure 3-8 Adding protected folders
- Select Add a protected folder. Specify the additional folders that you want to protect.
- Select Back.
- To configure trusted apps, click the Allow An App Through Controlled Folder Access link.
- Select Add An Allowed App. Specify the additional app(s) that you trust and select Open.
- Close Windows Security.
To use GPOs to add additional folders and apps to Controlled Folder Access, use the following procedure:
- On a domain controller, open the appropriate GPO for editing.
- In the Group Policy Management Editor, navigate to Computer Configuration > Policies > Administrative Templates > Windows Components > Microsoft Defender Antivirus > Microsoft Defender Exploit Guard > Controlled Folder Access.
- Select Configure Protected Folders and select Enabled. Select Show and enter each folder’s name.
- Select OK.
- Select Configure Allowed Applications and select Enabled. Select Show and enter each app’s path and name.
- Select OK.
- Close the Group Policy Editor.
To use Windows PowerShell to add protected folders, use the Add-MpPreference cmdlet. For example, to protect a folder named C:\MyDATA, use the following command:
Click here to view code image
Add-MpPreference -ControlledFolderAccessProtectedFolders “C:\MyDATA”
To use Windows PowerShell to add trusted apps, use the Add-MpPreference cmdlet. For example, to add a trusted app named C:\Apps\LOB\MyAPP.exe, use the following command:
Click here to view code image
Add-MpPreference -ControlledFolderAccessAllowedApplications “C:\Apps\LOB\MyAPP.exe”
Need More Review? Enable Controlled Folder Access
To review further details about configuring folder access, refer to the Microsoft website at https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/controlled-folders.



