Network location-based compliance policy
Managing devices is easy when they are confined within a traditional office setting. Administrators often find that once mobile devices are permanently away from the office and require access to corporate resources, the challenge of managing them can become more difficult.
Within the office, devices are provided with network access, such as wired Ethernet and secured Wi-Fi connections. Access to corporate resources via office-based devices is strictly controlled and monitored, with all user activity to cloud apps and web traffic subject to firewall constraints and corporate security and compliance scrutiny.
Using MDM, administrators can block access to a corporate network, app, or resource even when a device leaves a specific location. You must first define a location within Microsoft Endpoint Manager to provide this functionality.
To create a network location-based compliance policy (also known as network fencing), follow these steps:
- Sign into the Microsoft Endpoint Manager admin center at https://endpoint.microsoft.com as a global administrator.
- Select Devices, and then under Policy, click Compliance policies.
- On the Compliance policies page, select Locations.
- On the Locations page, select Create, as shown in Figure 2-2, and complete the following properties. Note that some properties are required, and some are optional, as noted below:
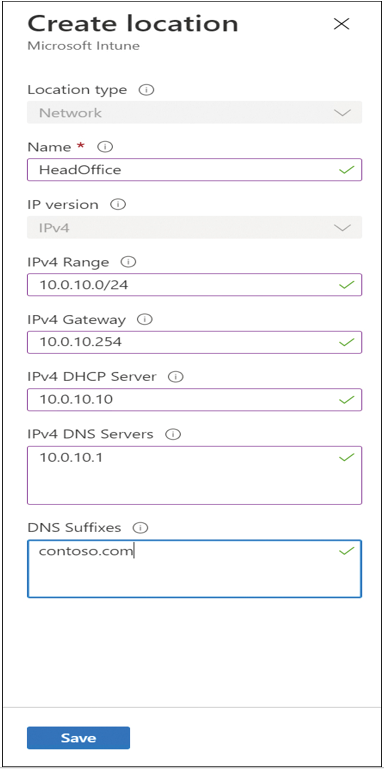
Figure 2-2 Create location
- Enter a name for the location, such as HeadOffice. (Required)
- Enter an IPv4 range with CIDR (Classless Interdomain Routing) notation, such as 10.0.10.0/24. If the device uses one of these IPv4 addresses, then the device will be deemed compliant. (Optional)
- Enter the IPv4 Gateway address, such as 10.0.10.254. (Optional)
- Enter the IPv4 DHCP Server address, such as 10.0.10.10. (Optional)
- Enter a list of IPv4 DNS Server addresses, such as 10.0.10.1. If the device uses one of these IPv4 DNS Server addresses, then the device will be compliant. (Optional)
- Enter a list of DNS Suffixes, such as contoso.com. If the device uses one of these DNS Suffixes, then the device will be compliant. (Optional)
- Click Save.
Once you have created one or more locations, you can create a policy to ensure devices must be connected to a trusted work network to be compliant. The policy can be used with conditional access policies to provide access to corporate resources only when the device is connected to the work network as defined in the location. Whenever the device moves away from the work network, the device becomes noncompliant and loses access to corporate resources.
If you are using Android devices that use the Android device administrator platform, you can create a standalone compliance policy that requires devices to be connected to your corporate network, which is assigned to the device or device group. This is then evaluated independently, or you can use an existing compliance policy and select a pre-defined location within the policy properties.
To add a location to an existing Android device administrator platform compliance policy, follow these steps:
- Sign into the Microsoft Endpoint Manager admin center at https://endpoint.microsoft.com as a global administrator.
- Select Devices, and then under Policy, click Compliance policies.
- On the Compliance policies blade, select an existing compliance policy that is targeting Android device administrator platform devices.
- Under Manage, click Properties.
- On the Properties blade, choose Locations and select Edit.
- On the Locations page, choose Select locations.
- From the list on the Select locations blade, choose the location and choose Select.
- Click Review + Save, and then on the Policy Properties page, click Save.
Once you have added a location in a compliance policy, if the device isn’t connected to the selected locations, then it’s immediately considered noncompliant.



