Requirements
To help protect against this possibility, 64-bit versions of both Windows 10 Enterprise and Windows 10 Education editions have a feature called Microsoft Defender Credential Guard, which implements a technology known as virtualization-assisted security; this enables Microsoft Defender Credential Guard to block access to credentials stored in the Local Security Authority.
In addition to requiring the appropriate edition of 64-bit editions of Windows 10, the following are the requirements for implementing Microsoft Defender Credential Guard:
- Support for virtualization-based security
- UEFI 2.3.1 or greater
- Secure Boot
- TPM 1.2 or 2.0, either discrete or firmware
- UEFI (firmware) lock preferred
- Virtualization features: Intel VT-x or AMD-V; SLAT (Second-Level Address Translation) must be enabled
- Windows hypervisor, although Hyper-V doesn’t need to be installed
Enable Microsoft Defender Credential Guard
After you have verified that your computer meets the requirements, you can enable Microsoft Defender Credential Guard by using Group Policy in an AD DS environment. On the domain controller, open the appropriate Group Policy Object (GPO) for editing and navigate to Computer Configuration > Policies > Administrative Templates > System > Device Guard. Enable Turn On Virtualization Based Security, as displayed in Figure 3-1.
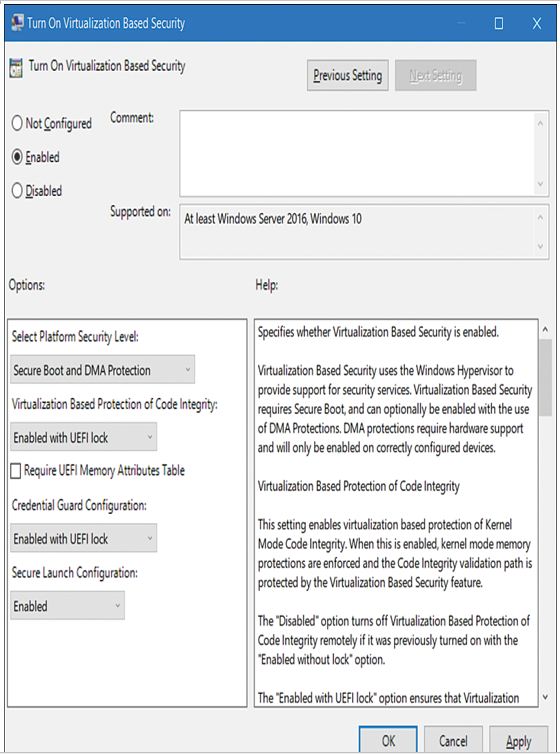
Figure 3-1 Enabling Microsoft Defender Credential Guard
Need More Review? Manage Windows Defender Credential Guard
To review further details about how Microsoft Defender Credential Guard works, refer to the Microsoft website at https://docs.microsoft.com/windows/security/identity-protection/credential-guard/credential-guard-manage.
Implement and manage Microsoft Defender Exploit Guard
You can use Microsoft Defender Exploit Guard, part of Microsoft Defender for Endpoint, to help to reduce the attack surface of your users’ apps. Microsoft Defender Exploit Guard consists of four components:
- Exploit protection Uses Microsoft Defender Antivirus or, if installed, third-party antivirus software to help mitigate exploit techniques used against your organization’s apps.
- Attack surface reduction rules Uses rules to help prevent attack vectors implemented by scripts, email, and Office-based malware. Based on Microsoft Defender Antivirus.
- Network protection Extends Microsoft Defender SmartScreen protection in Microsoft Edge to other applications to prevent access to internet domains that may host phishing scams, exploits, and other malicious content. Requires Microsoft Defender Antivirus and cloud-delivered protection enabled.
- Controlled folder access Helps protect against ransomware and malware by preventing changes to files in protected folders if the app attempting to make changes is malicious or exhibits suspicious behavior. Also requires Microsoft Defender Antivirus.
Note Microsoft Defender Test Ground Website
You can see these features in action at the following Microsoft website at https://demo.wd.microsoft.com/?ocid=cx-wddocs-testground.
You can manage and report on Microsoft Defender Exploit Guard by using the Windows Security app, as displayed in Figure 3-2.
Figure 3-2 Windows Security app
Table 3-1 identifies the Microsoft Defender Exploit Guard features available in each of the listed Windows 10 editions.
TABLE 3-1 Windows Defender Exploit Guard features
| Windows 10 edition | Features supported |
| Windows 10 Home | Exploit protection Controlled folder access |
| Windows 10 Pro | Exploit protection Controlled folder access |
| Windows 10 Enterprise E3 and Windows 10 Education E | Exploit protection Controlled folder access Network protection |
| Windows 10 Enterprise E5 and Windows 10 Education E | Exploit protection Controlled folder access Network protection Attack surface reduction rules |



